Transitioning from an OpenShift PoC to Production
Transitioning from an OpenShift Proof of Concept (PoC) to a production environment is a significant step that involves scaling up, ensuring high availability (HA), and implementing robust backup and recovery strategies.
It's essential to have a well-thought-out plan that addresses these aspects, along with security, change management, and collaboration across IT teams. Governance and processes must be established to manage the deployment effectively. Platform considerations, such as choosing the right infrastructure and determining resource allocation, are crucial.
To facilitate this transition, it's beneficial to leverage the expertise and solutions offered by industry leaders, such as the OpenShift solution developed in collaboration with Red Hat, which can streamline the process.

Additionally, understanding the differences between OpenShift and OKD, and the benefits of various installation tools, can provide insights into customizing the installation to fit the specific needs of a production environment.
OpenShift and OKD are both platforms that facilitate the deployment and management of containerized applications, but they cater to different user needs and scenarios.
OpenShift, provided by Red Hat, is an enterprise-level Kubernetes platform that offers a comprehensive suite of features, including
- Technical support,
- Security resources, and
- A partner ecosystem.
It is designed for businesses requiring a robust, supported environment with long-term support options, validated third-party operators, and certified databases and middleware.
OpenShift can be deployed across various infrastructures, including public clouds and on-premises servers, providing flexibility for hybrid and multicloud strategies.
On the other hand, OKD is the upstream community-driven counterpart of OpenShift, often a few releases ahead in terms of features, as it serves as the testing ground for new updates before they are incorporated into OpenShift. OKD is optimized for continuous application development and deployment, offering tools that support multiple programming languages and a cloud-native approach to application creation. While OKD provides a rich set of features for developers and operators, it does not come with the enterprise-grade support and certifications that OpenShift offers.
The choice between OpenShift and OKD depends on the specific needs of an organization.
If enterprise support, security, and certifications are critical, OpenShift is the preferred choice.
For organizations looking for a cutting-edge, community-supported version that allows for more experimentation and faster access to the latest features, OKD is the suitable option. Both platforms leverage the power of Kubernetes at their core, ensuring scalable and efficient container orchestration.
Understanding these differences can help organizations make an informed decision that aligns with their operational requirements and strategic goals. For further details, Red Hat provides a comprehensive comparison and insights into the unique advantages of each platform.
Understanding the Transition
The transition from a PoC to production involves scaling up from a small, controlled environment to a larger, more dynamic one. This process requires meticulous planning around several key areas:
- Scalability:
- Ensuring that the OpenShift environment can handle the increased load and traffic of a production setting.
- High Availability (HA):
- Setting up the system to be resilient against failures, with minimal downtime.
- Backup/Recovery:
- Implementing robust backup and recovery procedures to protect data integrity.
- Security:
- Strengthening security measures to protect against threats and vulnerabilities.
- Change Management:
- Establishing processes for managing changes and updates to the environment without disrupting services.
- Collaboration:
- Facilitating effective collaboration between IT units to ensure smooth operations.
Steps to Take
- Assessment:
- Evaluate the current PoC setup, identifying what works well and what needs improvement.
- Planning:
- Develop a detailed plan that covers all aspects of the production environment, including infrastructure, security, and compliance requirements.
- Infrastructure:
- Choose the right infrastructure that meets the demands of a production environment, whether it's on-premises, in the cloud, or a hybrid approach.
- Automation:
- Leverage tools like Ansible for automation to streamline deployment and operations processes.
- Testing:
- Conduct thorough testing to ensure the environment is stable and can handle production workloads.
- Monitoring:
- Implement monitoring tools to keep an eye on the system's performance and health.
- Governance:
- Set up governance policies to maintain control over the environment and ensure compliance with industry standards.
- Leveraging Expertise
- For organizations looking to accelerate this transition, partnering with experts who have experience in deploying OpenShift in production can be invaluable. Companies like HPE offer solutions that are jointly developed with Red Hat, providing a smoother path from PoC to production.
Moving from an OpenShift PoC to production is a complex but rewarding process. It requires careful consideration of various factors that impact the performance and reliability of the environment. By following a structured approach and possibly seeking expert assistance, organizations can successfully make this transition and reap the benefits of a production-ready OpenShift environment.
Transitioning from an OpenShift Proof of Concept (PoC) to a production environment is a pivotal phase that comes with its own set of challenges.
Here are some common hurdles that organizations may face during this process:
- Ensuring Scalability
- One of the primary concerns is ensuring that the OpenShift environment can scale to meet the demands of a production workload. This involves not just scaling up the infrastructure, but also ensuring that applications and services can handle the increased load without performance degradation.
- Achieving High Availability
- High availability is crucial in production. Organizations must design a system that is resilient to failures and can recover quickly to maintain service continuity. This often requires a multi-faceted approach, including redundant infrastructure, failover strategies, and robust monitoring.
- Implementing Robust Security Measures
- Security in a production environment is far more critical than in a PoC. Organizations need to implement strong security policies, conduct regular vulnerability assessments, and ensure compliance with security standards to protect sensitive data and services.
- Managing Data Integrity
- Data integrity is paramount, and the transition to production must include strategies for data backup and recovery. This ensures that in the event of a failure, data can be restored with minimal loss.
- Streamlining Change Management
- Change management becomes more complex as the environment scales. Organizations must establish clear processes for rolling out updates and changes without disrupting the production environment.
- Facilitating Collaboration
- Collaboration between various IT units becomes more challenging in a larger environment. Clear communication channels and collaboration tools are essential to ensure that all teams are aligned and working towards common goals.
- Navigating Network Complexity
- As the environment grows, so does the complexity of the network. Ensuring connectivity and network policy compliance in a hybrid, multi-cloud world can be daunting, requiring sophisticated network management solutions.
- Compliance with Regulations
- Adhering to regulatory requirements is a significant challenge, especially for industries that are heavily regulated. Organizations must ensure that their OpenShift production environment complies with all relevant laws and standards.
- Operational Complexity
- The operational complexity increases significantly when moving to production. Organizations must balance the need for advanced features and capabilities with the simplicity of operations to avoid overwhelming their teams.
- Resource Optimization
- Efficient resource utilization is key to controlling costs and maintaining performance. Organizations need to optimize their use of resources to ensure that the environment is cost-effective and sustainable.
The transition from an OpenShift PoC to production is a complex journey filled with challenges that require careful planning and execution. By being aware of these common challenges and preparing for them, organizations can smooth the path to a successful production deployment.
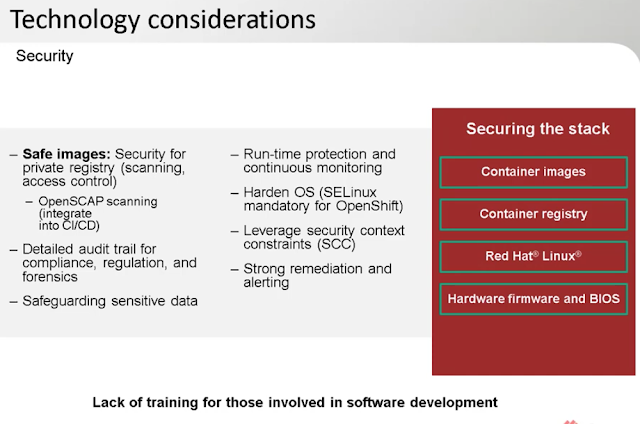
Addressing Security Challenges in Transitioning from OpenShift PoC to Production
When transitioning from an OpenShift Proof of Concept (PoC) to a production environment, addressing security challenges is paramount to protect your infrastructure, applications, and data. Here are some strategies to enhance security during this critical phase:
- Secure Containerization Practices
- Containerization offers numerous benefits, but it also introduces specific security challenges. It's essential to adopt secure containerization practices, such as using trusted base images, scanning for vulnerabilities, and implementing access controls for your container registry.
- Comprehensive Vulnerability Assessment
- Regularly assess the security of open-source products used within your organization. This involves evaluating features, security measures, and maintenance practices of these products to integrate trusted components into your supply chain.
- Implementing OpenSCAP Scanning
- Integrate OpenSCAP scanning into your Continuous Integration/Continuous Deployment (CI/CD) pipeline. This helps in identifying and mitigating known vulnerabilities and ensures compliance with security benchmarks.
- Detailed Audit Trails
- Maintain detailed audit trails for compliance, regulation, and forensics. This provides visibility into the actions performed within your OpenShift environment and aids in investigating security incidents.
- Run-Time Protection and Monitoring
- Implement run-time protection and continuous monitoring to detect and respond to threats in real-time. This includes safeguarding sensitive data and monitoring network traffic for suspicious activities.
- Harden the Operating System
- Ensure that the operating system hosting your OpenShift environment is hardened. Use security-enhanced Linux (SELinux) policies to enforce mandatory access controls and limit potential attack vectors.
- Leverage Security Features of OpenShift
- OpenShift provides various built-in security features. Make use of these, such as Role-Based Access Control (RBAC), Security Context Constraints (SCC), and network policies to enforce security at different layers.
- Data Encryption
- Encrypt sensitive data both at rest and in transit. This helps in protecting data confidentiality and integrity, even if unauthorized access occurs.
- Security Training for Staff
- Provide security training for your staff to ensure they are aware of best practices and the specific security protocols related to OpenShift. A well-informed team is a critical defense against security breaches.
- Partner with Security Experts
- Consider partnering with security experts who have experience with OpenShift deployments. They can provide insights and assistance in setting up a secure production environment.
Security is a critical aspect of transitioning from an OpenShift PoC to production. By implementing these strategies, organizations can address the various security challenges that arise during this transition. It's important to stay informed about the latest security trends and continuously improve your security posture to safeguard your OpenShift environment against evolving threats.
Best Practices for Implementing RBAC in OpenShift
Role-Based Access Control (RBAC) is a critical component in managing access to resources within an OpenShift environment. It allows administrators to regulate who can do what within a project or across the cluster.
Here are some best practices for implementing RBAC in OpenShift:
- Principle of Least Privilege
- Always follow the principle of least privilege. This means giving users only the access that they need to perform their jobs and no more. This minimizes the risk of accidental or malicious changes that can affect the system's stability and security.
- Use Predefined ClusterRoles
- OpenShift comes with a set of predefined ClusterRoles that are designed to meet common use cases and provide a good starting point for defining access controls. Use these roles whenever possible to take advantage of OpenShift's built-in security policies.
- Avoid Overly Broad Permissions
- Be cautious when assigning ClusterRoles for namespaced resources. ClusterRoles are powerful and can grant access across the entire cluster, which might be more than what is necessary for a particular user or service account.
- Service Account Management
- Use specific service accounts for applications instead of default service accounts. This helps in tracking and controlling the actions performed by applications and enhances security by limiting potential access.
- Group Management
- Manage bindings through groups rather than individual user accounts where possible. This simplifies the management of access controls and makes it easier to update permissions for multiple users at once.
- Regular Audits and Reviews
- Regularly review and audit your RBAC configurations to ensure that they still align with the current needs and security policies. This practice helps in identifying and rectifying any excessive permissions that might have been granted over time.
- Use Role Bindings Wisely
- Role bindings can be created at both the project level (local role bindings) and the cluster level (cluster role bindings). Ensure that you are using the appropriate level of binding for the roles you are assigning to maintain proper scope of access.
- Custom Roles
- Create custom roles if the predefined roles do not fit your organization's specific needs. Custom roles can be tailored to provide exactly the permissions needed without any excess.
- Documentation and Policy
- Document your RBAC policies and keep them updated. Clear documentation helps team members understand their access levels and the reasoning behind them, which is essential for maintaining security and compliance.
- Utilize RBAC Tools
- Leverage RBAC tools and features provided by OpenShift, such as the RBAC reconciliation commands, which help ensure that any customizations to roles do not drift from their intended permissions over time.
Implementing RBAC in OpenShift requires careful planning and ongoing management to ensure that access controls are effective and secure. By following these best practices, administrators can create a robust RBAC strategy that protects resources and aligns with the organization's operational requirements.
Congratulations! You've now journeyed through the essential chapters of transitioning from PoC to production with OpenShift.
By harnessing the power of containerization, DevOps practices, and cutting-edge technologies, you're well-equipped to drive business efficiency and innovation with OpenShift.
Are you ready to take the next step in your OpenShift journey?
If you're looking for a complete guide to mastering OpenShift deployments, we've got you covered. Simply fill out the form below, and we'll send you a free detailed ebook guide of POC to production with OpenShift. Let's embark on this exciting journey together and unlock the full potential of OpenShift for your business!
Feel free to reach out to us with any questions or inquiries. We're here to help you succeed in your OpenShift endeavors. Happy deploying!
[Form: Enter your email to receive your free detailed ebook guide of POC to production with OpenShift]